Blog / Disruptive Technologies
Biometric Security: Is it safe?
Categories

Did you use any biometric security to read this post or to get into your office this morning? Biometrics are fast becoming a preferred way to access devices, applications, and facilities. Leading smartphone companies such as Apple and Samsung have made fingerprint and facial recognition a simple method of identification and authentication for their devices. Technology advances in processing power, camera resolution, and illumination are making biometrics more common, particularly, Iris scanning, which has moved from a niche element of high-end security systems, to a broader commercial and consumer application. With this premise, what is our exposure when we use our body to interact with the digital world?
Biometric Security: How it works
Biometrics delivers significant advantages preventing cybercrime. Nowadays, biometrics security is mainstream to prevent unlawful facility access; preserve data privacy and avoid threat actors from perpetrating identity fraud and identity theft with phishing, social engineering and other techniques. Biometric technology encompasses two stages: enrollment - a process of scanning the body for the first time (Iris, Fingerprint, Voice, Face, DNA) and storing it in a database as reference for future authorizations; and verification- a process of re-scan and verifying the database for a match.
Enrollment and Verification process. Source: Wencheng Yang - ResearchGate
Biometric Security: 3 risks to be aware of
As good as it all seems, these technologies also bring some risks. I’ve identified three issues which individuals and organizations need to be aware-of to protect themselves and the digital information they own:
The first risk involves the biometric footprint that we leave behind in the database associated with the enrollment process. Now imagine a file with our unique biometric data profile. As with passwords, we have no control over this “digital picture” of us, however, unlike a password, biometrics cannot be changed if lost, stolen or mishandled. In addition, in some cases, these files are not adequately protected with encryption using digital certificates, and have no validity expirations built in.
The second risk has to do with biometric spoofing”. Yes, same as in spy movies. With 3D printing and other techniques as simple as a picture or video, we can reconstruct the biometric element and use it without the presence of the individual. A fraudster might use biometric spoofing attacks to impersonate someone in order to defeat biometric authentication mechanism.
The third risk relates to the additional liability that organizations incur when storing this type of data. The risk relates to the biometric footprint for “voluntary” registration. As in the case of facility access systems. Also, having this type of data as a byproduct of our activity, may pose an involuntary risk. For instance hospitals, that hold patient samples or DNA profiles. In face of a strong personal data privacy regulation, organizations must gage the security implications of a potential data breach, and the potential liability.
Conclusion: Embrace it, but cover yourself!
Biometrics has the capacity to increase confidence in personal identification and authentication. The main difference with traditional passwords and tokens, is that biometrics works on the premise of a direct link between the system and the individual (strong binding), whereas the indirect link characterized by passwords and tokens (weak binding).
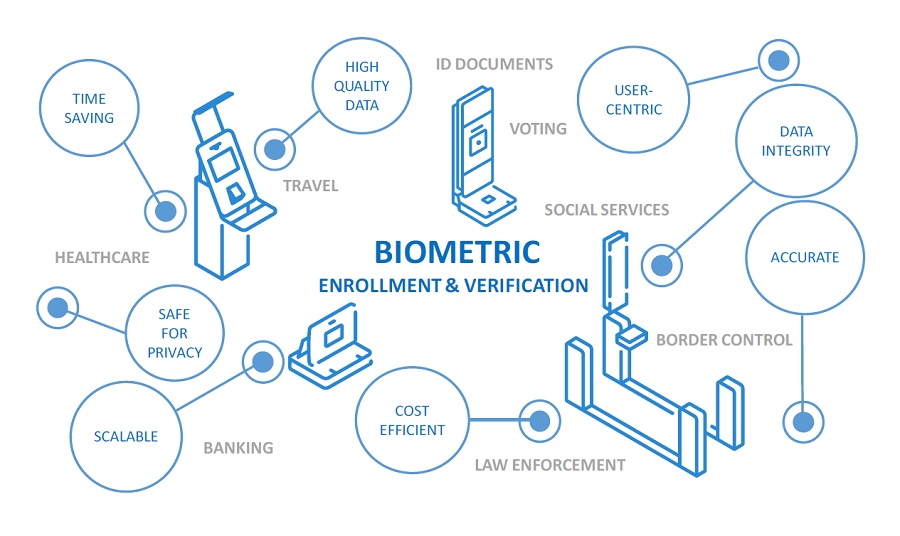
Biometric security has uses and advantages in varios industries. Source: Vbbackoffice. The mainstream use of biometric security opens the door to new risks for individuals involving identity fraud, identity theft and cybercrime. The primary concern enfolds the potential case of having biometric data profiles (Iris, Fingerprint, Voice, Face, DNA) stolen or reproduced without knowledge and consent, an the inability of companies or individuals to easily correct the situation. For that reason, it's important to deploy safety strategies, such as divide-and-conquer algorithms, and to polish cybersecurity skills, like risk analysis and complex thinking. One thing is for certain: biometric security is here to stay, and we have to embrace it in the best possible way.
Transform your business with (safe!) disruptive technologies
If you want to live up to today’s rapidly changing business landscape, sharpening your competitive edge, it's important to reshape your company & your mindset through innovation. That's precisely the focus of our MBA in Digital Transformation. In that programme, Gonzalo Cuatrecasas, author of this article, teaches students cybersecurity and digital business security, so you can deploy disruptive technologies in a strategic and safe way.





